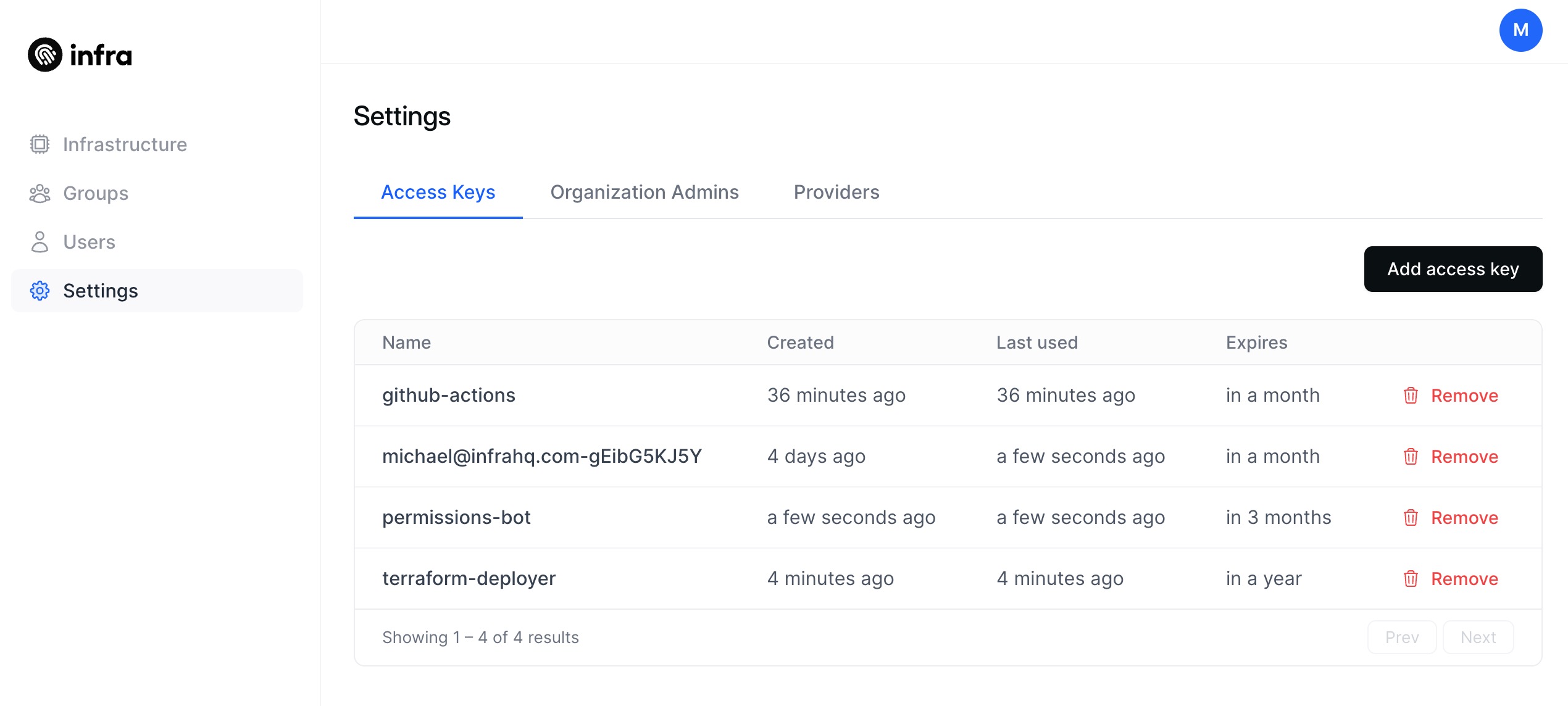
Infra's access keys can now be generated in the dashboard. This unlocks many use cases. Some examples include:
- Dynamically changing/revoking permissions for users and groups
- CI/CD infrastructure access (i.e. GitHub Actions)
- Other actions that can be performed via Infra's API.
Caveats:
Currently, access keys share the same permissions as the user who created it. This is not very ideal for users who want to have scoped keys that have dedicated use cases. This problem will be addressed in the future.
For now, it is advisable to create another user, assign only limited permissions for that user, and login as that user to generate an access key for usage. Once this is created, the administrator account can be used to scope the permissions of that user (or multiple users).
Improved Kubeconfig support for multiple namespaces
For Kubernetes clusters where a user/group has access to multiple individual namespaces, only one kubeconfig context will be created for a single cluster. Previously, if a user had access to multiple namespaces within a cluster, the user will receive a context for each individual namespace.
CLI quality of life improvements
- Change access keys to make their names unique to a specific user, instead of for an entire org
- Make
infra keys listdefault to the current user - Add an
--allflag toinfra keys listfor admins which can list all access keys in the org - Make
infra keys addnot require a user name - Add a
--user=argument toinfra keys addto be consistent withinfra keys list - Add a
--connectorflag toinfra keys addto create the key for a connector - Make
infra keys removeto be specific to the current user - Add a
--user=argument similar toinfra keys listandinfra keys add - Changed the API to call
DELETE /api/access-keys/:idinstead ofDELETE /api/access-keys - Added
LastUsedfield to the API and updatedinfra keys listto show the last time a specific key was used
Bug fixes & improvements
- Fixed an issue where checkboxes would not show a checkmark in the Dashboard
- Identity providers are now configured under Settings
- Added ability to remove access to multiple namespaces at the same time in the Infra Dashboard
- Fixed issue where logging in with a temporary password would result in an error